
We are pleased to announce the release of mORMot 2.1.
The download link is available on github.

The mORMot family is growing up.
2023-08-24
2023-08-24. Open Source › mORMot Framework

We are pleased to announce the release of mORMot 2.1.
The download link is available on github.

The mORMot family is growing up.
2016-12-19
2016-12-19. Open Source › mORMot Framework
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact
and self-contained way for securely transmitting information between parties as
a JSON object. This information can be verified and trusted because it is
digitally signed. JWTs can be signed using a secret (with the HMAC algorithm)
or a public/private key pair using RSA or ECDSA.
They can be used for:
JWT to any HTTP request allows
Single Sign On user validation across different domains;See http://jwt.io for an introduction to JSON Web Tokens.
Our mORMot framework now implements JWT:
HS256 (HMAC-SHA256) and ES256 (256-bit ECDSA)
algorithms (with the addition of the "none" weak algo);HS256
verification under x64), with optional in-memory cache if needed (e.g. for
slower ES256);dll, works
with Delphi or FPC);2016-09-24
2016-09-24. Open Source › mORMot Framework
After weeks of implementation and testing, we introduce today a new feature of our mORMot Open-Source Framework.
Asymmetric encryption, also known as public-key cryptography, uses pairs of keys:
The framework
SynEcc unit features a full asymmetric encryption system, based on
Elliptic curve
cryptography (ECC), which may be used at application level (i.e. to
protect your application data, by signing or encrypting it), or at transmission
level (to enhance communication safety).
A full set of high-level features, including certificates and command line
tool, offers a stand-alone but complete public-key
infrastructure (PKI).
2016-05-14
2016-05-14. Open Source › mORMot Framework
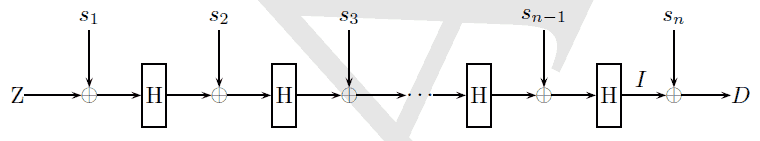
In any modern application, especially on
Client/Server nTier architecture as our little mORMot offers, we
often have to persist some private keys in a safe way.
Problem with such keys is that they consist in small amount of bytes (typically
16 or 32 bytes), easy to be left somewhere in disk or memory.
Given the abilities of recent forensic data recovery
methods, data can't be destroyed on magnetic or flash storage media
reliably.

We have just added to our SynCrypto OpenSource library
the Anti-forensic Information Splitter algorithm, as proposed in
TKS1, and implemented in the LUKS
standard.
LUKS is the de-facto standard of platform-independent standard on-disk
format for use in various tools.
2015-02-21
2015-02-21. Open Source › Open Source libraries
We have just included some optimized x64 assembler to our Open
Source SynCrypto.pas unit
so that SHA-256 hashing will perform at best speed.
It is an adaptation from
tuned Intel's assembly macros, which makes use of the SSE4 instruction set,
if available.
