You like working with mORMot ? We're hiring new developers at LiveMon. We're a full-remote team (with a monthly gather-up in Paris), working on a real-time AI-powered monitoring tool. I joined LiveMon this week, and we will work together on this exciting project, using mORMot and FPC! Contact us at […]
Tag - Delphi
2017-10-24
EKON 21 Slides
2017-10-24. Open Source › mORMot Framework
After having enjoyed EKON 21 conferences in Köln, some quick post to share material about my presentations. MicroServices: SOLID Meets SOA MicroServices: Event-Driven Design Practical Domain-Driven Design I also included the "Practical DDD" source code in a new sample folder of the mORMot […]
2017-08-10
Faster and cross-platform SynLZ
2017-08-10. Open Source › mORMot Framework
You probably know about our SynLZ compression unit, in pascal and x86 asm, which is very fast for compression with a good compression ratio, and proudly compete with LZ4 or Snappy. It is used in our framework everywhere, e.g. for WebSockets communication, for ECC encrypted file content, or to […]
2017-03-22
Delphi 10.2 Tokyo Compatibility: DCC64 broken
2017-03-22. Open Source › mORMot Framework
We are proud to announce compatibility of our mORMot Open Source framework
with the latest Delphi 10.2 Tokyo compiler...
At least for Win32.
For Win64, the compiler was stuck at the end of the compilation, burning 100% of one CPU core...

A bit disappointing, isn't it?
2017-03-18
Application Locking using Asymmetric Encryption
2017-03-18. Open Source › mORMot Framework
A common feature request for professional software is to prevent abuse of
published applications.
For licensing or security reasons, you may be requested to "lock" the execution
of programs, maybe tools or services.
Our Open-Souce mORMot framework can leverage
Asymmetric Cryptography to ensure that only allowed users could run some
executables, optionally with dedicated settings, on a given computer.
It offers the first brick on which you may build your own system upon.
From the User point of view, he/she will transmit
a user@host.public file, then receives a corresponding
user@host.unlock file, which will unlock the application.
Pretty easy to understand - even if some complex asymmetric encryption is
involved behind the scene.
2016-12-19
JSON Web Tokens (JWT)
2016-12-19. Open Source › mORMot Framework
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact
and self-contained way for securely transmitting information between parties as
a JSON object. This information can be verified and trusted because it is
digitally signed. JWTs can be signed using a secret (with the HMAC algorithm)
or a public/private key pair using RSA or ECDSA.
They can be used for:
- Authentication: including a
JWTto any HTTP request allows Single Sign On user validation across different domains; - Secure Information Exchange: a small amount of data can be stored in the JWT payload, and is digitally signed to ensure its provenance and integrity.
See http://jwt.io for an introduction to JSON Web Tokens.
Our mORMot framework now implements JWT:
HS256(HMAC-SHA256) andES256(256-bit ECDSA) algorithms (with the addition of the"none"weak algo);- Validates all claims (validation dates, audiences, JWT ID);
- Thread-safe and high performance (2 µs for a
HS256verification under x64), with optional in-memory cache if needed (e.g. for slowerES256); - Stand-alone and cross-platform code (no external
dll, works with Delphi or FPC); - Enhanced security and strong design - per instance, it is by design immune from https://auth0.com/blog/2015/03/31/critical-vulnerabilities-in-json-web-token-libraries
- Full integration with the framework.
2016-11-10
EKON20 mORMot Conferences
2016-11-10. Open Source › mORMot Framework
EKON20 is now over, and there was a lot of people, great speakers, beautiful T-Shirt, and fresh beer! I've published the slides of my mORMot conferences on SlideShare... EKON20 From RAD to SOA with mORMot EKON20 mORMot Legacy Code Technical Debt Delphi Conference EKON20 Ride a mORMot EKON20 2016 […]
2016-09-24
Public-key Asymmetric Cryptography via SynECC
2016-09-24. Open Source › mORMot Framework
After weeks of implementation and testing, we introduce today a new feature of our mORMot Open-Source Framework.
Asymmetric encryption, also known as public-key cryptography, uses pairs of keys:
- Public keys that may be disseminated widely;
- Paired with private keys which are known only to the owner.
The framework
SynEcc unit features a full asymmetric encryption system, based on
Elliptic curve
cryptography (ECC), which may be used at application level (i.e. to
protect your application data, by signing or encrypting it), or at transmission
level (to enhance communication safety).
A full set of high-level features, including certificates and command line
tool, offers a stand-alone but complete public-key
infrastructure (PKI).
2016-09-06
Ride the mORMot at EKON 20 in Dusseldorf!
2016-09-06. Open Source › mORMot Framework

There are still a few days for "very early birds" offer for EKON 20 conference, and meet us for 3 sessions (including a half-day training/introduction to mORMot)! Join us the 7-9th of November in Düsseldorf! Our sessions are not restricted to mORMot, but will use mORMot to illustrate some […]
2016-05-14
Anti-forensic, safe storage of private keys
2016-05-14. Open Source › mORMot Framework
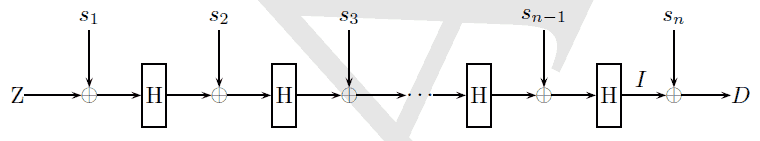
In any modern application, especially on
Client/Server nTier architecture as our little mORMot offers, we
often have to persist some private keys in a safe way.
Problem with such keys is that they consist in small amount of bytes (typically
16 or 32 bytes), easy to be left somewhere in disk or memory.
Given the abilities of recent forensic data recovery
methods, data can't be destroyed on magnetic or flash storage media
reliably.

We have just added to our SynCrypto OpenSource library
the Anti-forensic Information Splitter algorithm, as proposed in
TKS1, and implemented in the LUKS
standard.
LUKS is the de-facto standard of platform-independent standard on-disk
format for use in various tools.
2016-04-22
Support of Delphi 10.1 Berlin
2016-04-22. Open Source
You should have noticed that Delphi 10.1 Berlin has been released. Our Open Source projects, including mORMot and SynPDF and their associated documentation have been updated to support this new revision. Any additional feedback is welcome, as usual!
2016-04-09
AES-256 based Cryptographically Secure Pseudo-Random Number Generator (CSPRNG)
2016-04-09. Open Source › mORMot Framework
Everyone knows about the pascal random()
function.
It returns some numbers, using a linear
congruential generator, with a multiplier of 134775813,
in its Delphi implementation.
It is fast, but not really secure. Output is very predictable, especially if
you forgot to execute the RandSeed()
procedure.

In real world scenarios, safety always requires random numbers, e.g. for
key/nonce/IV/salt/challenge generation.
The less predictable, the better.
We just included a Cryptographically
Secure Pseudo-Random Number Generator (CSPRNG) into our
SynCrypto.pas unit.
The TAESPRNG class would use real system entropy to generate
a sequence of pseudorandom bytes, using AES-256, so returning highly
unpredictable content.
2016-02-08
Linux support for Delphi to be available end of 2016
2016-02-08. Pascal Programming
Marco Cantu, product manager of Delphi/RAD Studio, did publish the
official RAD Studio 2016 Product Approach and Roadmap.
The upcoming release has a codename known as "BigBen", and should be called
Delphi 10.1 Berlin, as far as I understand.

After this summer, another release, which codename is "Godzilla", will
support Linux as a compiler target, in its Delphi 10.2 Tokyo release.
This is a very good news, and some details are given.
I've included those official names to mORMot's internal compiler version
detection.
Thanks Marco for the information, and pushing in this direction!
My only concern is that it would be "ARC-enabled"...
2016-01-09
Safe locks for multi-thread applications
2016-01-09. Open Source › mORMot Framework
Once your application is multi-threaded, concurrent data access should be
protected. We already wrote about how debugging multi-thread
applications may be hard.
Otherwise, a "race
condition" issue may appear: for instance, if two threads modify a variable
at the same time (e.g. decrease a counter), values may become incoherent and
unsafe to use. Another symptom of broken logic is the "deadlock", by which the whole
application appears to be blocked and unresponsive, when two threads have a
wrong use of the lock, so are blocking each-others.
On a server system, which is expected to run 24/7 with no maintenance, such
issues are to be avoided.
In Delphi, protection of a resource (which may be an object, or any
variable) is usually done via Critical
Sections.
A critical section is an object used to make sure, that some part of
the code is executed only by one thread at a time. A critical section
needs to be created/initialized before it can be used and be released when it
is not needed anymore. Then, some code is protected using Enter/Leave
methods, which would lock its execution: in practice, only a single
thread would own the critical section, so only a single thread would
be able to execute this code section, and other threads would wait until the
lock is released. For best performance, the protected sections should be as
small as possible - otherwise the benefit of using threads may be voided, since
any other thread would wait for the thread owning the critical section
to release the lock.
We will now see that Delphi's TCriticalSection may have
potential issues, and what our framework proposes to ease critical
section use in your applications.
2015-12-11
Audit Trail for Services
2015-12-11. Open Source › mORMot Framework
We have seen previously how the ORM part of the framework is able to provide
an Audit
Trail for change tracking.
It is a very convenient way of storing the change of state of the data.
On the other side, in any modern SOA solution, data is not at the center any
more, but services.
Sometimes, the data is not stored within your server, but in a third-party
Service-Oriented Architecture (SOA).
Being able to monitor the service execution of the whole system becomes sooner
or later mandatory.
.jpg)
Our framework allows to create an Audit Trail of any incoming or outgoing service operation, in a secure, efficient and automated way.
2015-11-21
Try to avoid RTTI (ab)use
2015-11-21. Pascal Programming
There is a very trendy move, since a few years, to value so called "meta-programming".
In short, it is about the ability to treat programs as their data.
It is a very powerful paradigm in functional languages, and it was also
introduced to OOP languages, even in SmallTalk a long time
before this concept was trendy in Ruby, C# or Java.
In OOP compiled languages, reflection is used to achieve a similar behavior
at run-time, mainly via RTTI (Run-Time Type
Information).
Delphi supports
RTTI since its version 1, as it was heavily used e.g. for all UI
streaming.
In our framework, we rely on RTTI for its main features:
ORM, SOA
and
MVC - and even in some other parts, like
Desktop UI generation.
But RTTI could easily be abused.
Here are some thoughts, started as a comment in a
good old Mason's blog article about how RTTI performance may be a
bottleneck.
My comment was to get rid of RTTI, and follow a SOLID
implementation with explicit OOP code, like use of
interface.
2015-11-17
Benefits of interface callbacks instead of class messages
2015-11-17. Open Source › mORMot Framework
If you compare with existing client/server SOA solutions (in Delphi, Java,
C# or even in Go or other frameworks), mORMot's
interface-based
callback mechanism sounds pretty unique and easy to work with.

Most Events Oriented solutions do use a set of dedicated
messages to propagate the events, with a centralized Message
Bus (like MSMQ or
JMS), or a
P2P/decentralized approach (see e.g. ZeroMQ or NanoMsg). In practice, you are expected to
define one class per message, the class fields being
the message values. You would define e.g. one class to notify a
successful process, and another class to notify an error. SOA
services would eventually tend to be defined by a huge number of individual
classes, with the temptation of re-using existing classes in several
contexts.
Our interface-based approach allows to gather all events:
- In a single
interfacetype per notification, i.e. probably per service operation; - With one method per event;
- Using method parameters defining the event values.
Since asynchronous notifications are needed most of the time, method
parameters would be one-way, i.e. defined only
as const - in such case, an evolved algorithm would
transparently gather those outgoing messages, to enhance scalability when
processing such asynchronous events. Blocking request may also be defined
as var/out, as we will see below, inWorkflow
adaptation.
Behind the scene, the framework would still transmit raw messages over IP
sockets (currently over a
WebSockets connection), like other systems, but events notification would
benefit from using interfaces, on both server and client sides.
We will now see how...
2015-10-23
Letters of Hope
2015-10-23. Pascal Programming
As we already notified in this blog, Embarcadero has been finally bought by IDERA. Delphi users received a letter from Randy Jacops, IDERA CEO. Written in my mother language, in perfect French. Nice! The letter states that they have 20,000 customers... It sounds more realistic than the numbers […]
2015-10-05
Delphi 10 Seattle Win64 compiler Heisenbug: unusable target
2015-10-05. Pascal Programming
Andy reported that he was not able to validate its IDE fix pack for Delphi 10 Seattle, due to its Win64 compiler not being deterministic anymore. The generated code did vary, from one build to other. Sadly, on our side, we identified that the code generated by the Win64 compiler of Delphi 10 Seattle […]
2015-09-28
mORMot show case: Illustrated Spare Parts Catalog
2015-09-28. Open Source › mORMot Framework
Illustrated Spare Parts Catalog is, as its name suggests, a software for creating and publishing spare parts catalogs. It uses mORMot for client-server communication and ORM, and SynPdf for the reporting. Sounds like a powerful solution. It is also a testimony that you could use big databases (20 GB […]
« previous entries - page 3 of 18 - next entries »



